Two-factor authentication adds an extra layer of defense against hackers—even if your password is stolen or guessed, another checkpoint will block account access. I regularly recommend enabling 2FA as a wise security move, especially for any valuable accounts (e.g., primary email address, banking services, etc.). But unfortunately, 2FA isn’t failproof.
Truthfully, no security measure is. For 2FA, attackers have discovered ways to sidestep the stronger protection. Whether exploiting human weaknesses or known system vulnerabilities, the effect is similar to kicking a door down to get past the deadbolt.
The good news: Knowing how common forms of 2FA can be bypassed will help you avoid a hacker’s tricks—and continue getting the full benefit of having 2FA at your back. Think of it akin to swapping in a stronger strike plate and longer screws on your front door.
Stolen text messages

Olha Ruskykh / Pexels
The simplest form of two-factor authentication is receiving one-time codes over text message. This method is also considered one of the weakest forms of 2FA because texts can be intercepted in a couple of different ways.
The more well-known one is SIM jacking, where a hacker steals your whole phone number from you. Basically, it gets transferred unbeknownst to you; the attacker contacts your carrier and has your phone number linked to a new SIM card (or eSIM). They will then receive all of your text messages, including 2FA codes.
The other method is known as an SS7 attack, in which the SMS message is redirected. You’ll never know it was sent to you, nor that someone else received it instead. Because of how messaging protocols work, you can’t directly avoid this kind of attack.
How to avoid: To guard against SIM jacking, contact your phone carrier’s customer support (or look in your account settings) and ask if you can create a special account PIN or password—one that will be required for any account changes, including switching to a new SIM card.
But the better protection is to choose a different method of 2FA, which also solves the issues with SS7 attacks. Text-based 2FA’s weaknesses are inherent to how our telecommunication systems work.
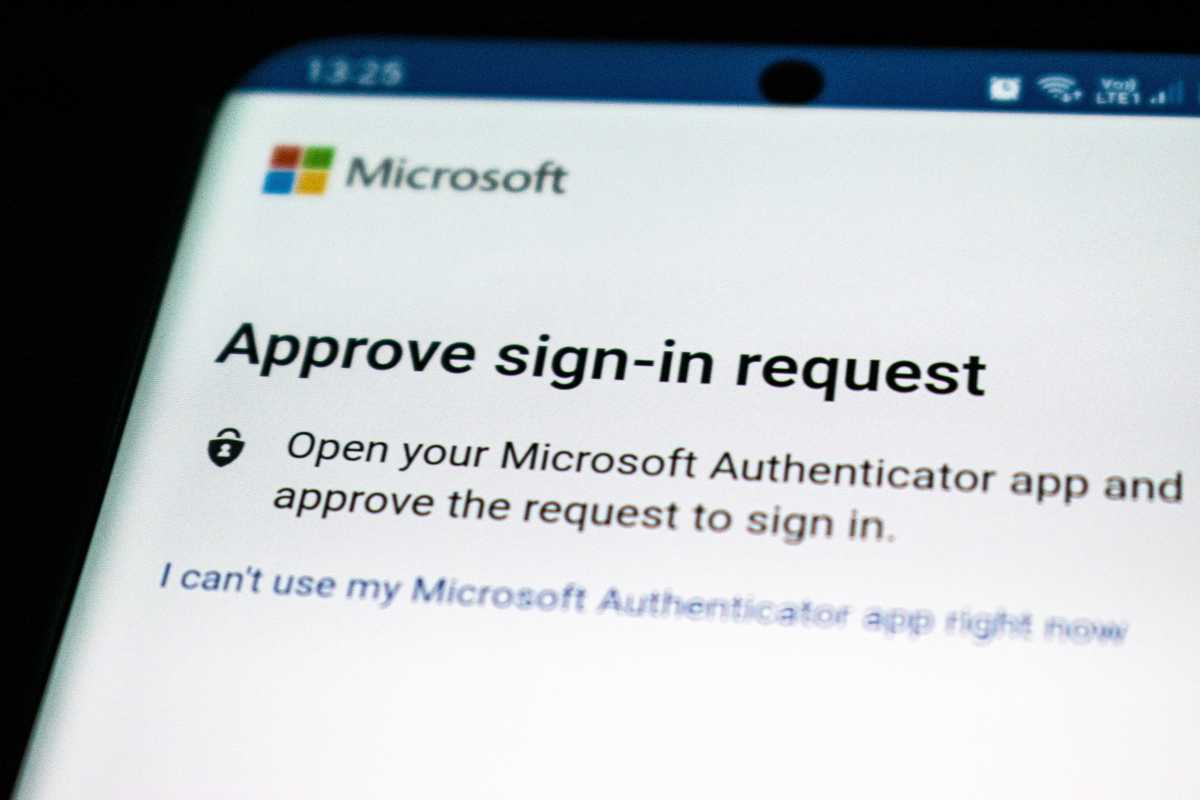
Approval spamming
Ed Hardie / Unsplash
One reasonably strong form of two-factor authentication is through a type of app that sends a push notification to your phone, asking for permission to authorize new devices. If you approve the request, account access is granted.
Attackers can weaponize this notification system. By flooding a phone or device with requests, the user could give approval without truly meaning to—either due to fatigue from the flood, or accidentally pressing the wrong button while clearing notifications.
How to avoid: Use unique, strong passwords for your accounts. Also be on the lookout for phishing attacks. If an attacker can’t steal, guess, or hack your password, they can’t spam you with approval requests.
(And if you ever find yourself experiencing this type of 2FA fatigue attack, change your account password immediately. Use an alternative method of 2FA verification, like a saved backup code, if you have to log into your account first to do so.)
Phishing
One-time use 2FA codes can be used by anyone, no matter if delivered via text message or generated in an app. That means if you read the code over the phone or send a screenshot to someone else, they can get into your account if they have the password.
Phishing attacks can steal both your password and your two-factor authentication codes—if you type or enter that info into a fake or compromised login page, a hacker then can use your credentials. The same applies if someone calls you and asks for the current 2FA code showing in your app.
How to avoid: Refuse to give your code to anyone who asks. Be cautious about which websites you visit and the forms you fill out. Also, don’t download apps or browser extensions not widely recommended by experts. You can accidentally install malware on your device that will silently steal your 2FA codes.
FIDO key bypass

Jared Newman / Foundry
Security keys (like Yubikeys) are considered the most secure form of two-factor authentication. You have to be physically present to use one and successfully authenticate during the 2FA verification step—you have to press a button on the key at the right time. Unless an attacker gets their hands on your security key, they can’t use it.
So how can this 2FA method become compromised? A weaker form of 2FA. Some services allow verifying new devices from an already authorized device. So maybe you first logged in and used your Yubikey to do so, but now you deal with subsequent requests by using your existing device to authenticate.
Hackers can then launch an approval spamming attack, just as outlined above.
How to avoid: Disable this login method for your account. Stick to just the security key as the method of 2FA authentication.
Connectez-vous pour ajouter un commentaire
Autres messages de ce groupe

If you’ve been exhausted by the unstoppable deployment of AI chatbots

If you’re concerned that your favorite may be subsumed by the growing

I have yet to see an OLED gaming monitor go below the $400 mark, and


Split keyboards are hard to find, especially if you’re looking for so

If you want to upgrade your budget PC gaming setup without shelling o