I have bad news for everyone with weak passwords. A hacker can guess your laziest random passwords in the same amount of time it takes to watch a movie.
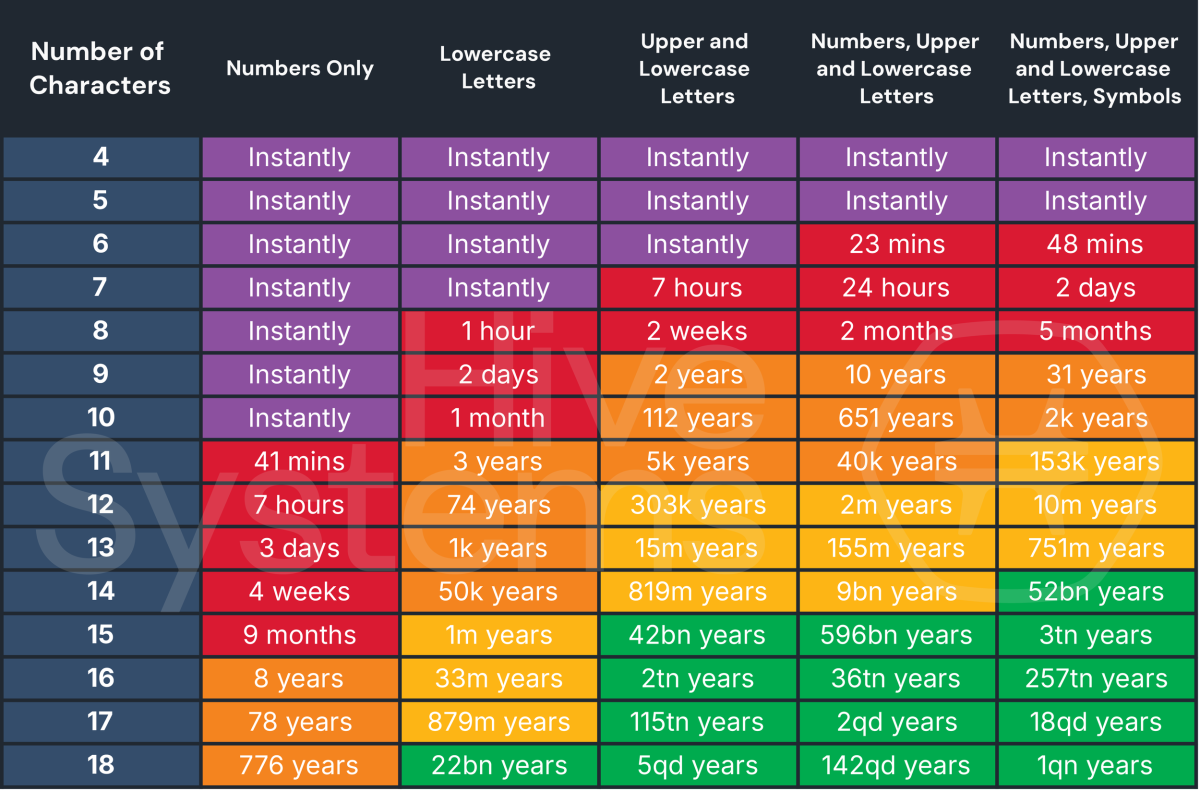
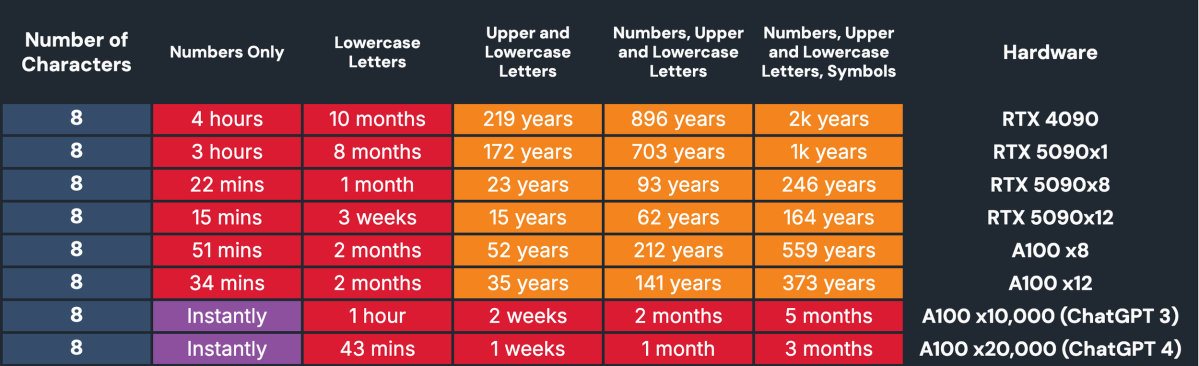
It turns out when you put the most brutally fast consumer graphics card on the task of, uh, brute-forcing 8-character passwords, it can crack a numbers-only string in 3 hours.
Such is the finding of Hive Systems, a cybersecurity firm based in Virginia, as part of the research that went into its 2025 password table. (Hat tip to HotHardware for spotting the news.) The chart shows how fast a “consumer budget” hacker could brute-force passwords of varying lengths (4 to 18 characters) and compositions (e.g., numbers only, lowercase letters, uppercase and lowercase letters, etc.).
And actually, “consumer budget” means twelve RTX 5090s racing to uncover your password, not just one. But looking at the work of just one is already startling enough.
Hive Systems
These days, an 8-character password is the default minimum across a majority of websites. Anyone who stuck to that baseline and mashed on their keyboard’s numpad is at high risk for getting hacked.
And while the complexity of a password improves the situation, with hours turning into months, years, and even a whole millennium as you scale up, it doesn’t quite save you from danger.
Because this is what it looks like when you casually put $30,000 of graphics card power (give or take, depending on the RTX 5090 model selected by our hypothetical hacker):

Hive Systems
An 8-character password made up of just numbers can be cracked instantly and lowercase letters in 3 weeks. And remember, that’s random lowercase letters, not a word. If you choose words that can be found in the dictionary or were stolen in a breach, it’s instantly game over.
Usually, if you’re not using a password manager, you’re probably keeping your passwords as simple as possible, if not outright reusing some. Hopefully not any tied to your financial accounts—the reason why a $30K+ investment is nothing to a hacker using this kind of attack.
Hive Systems
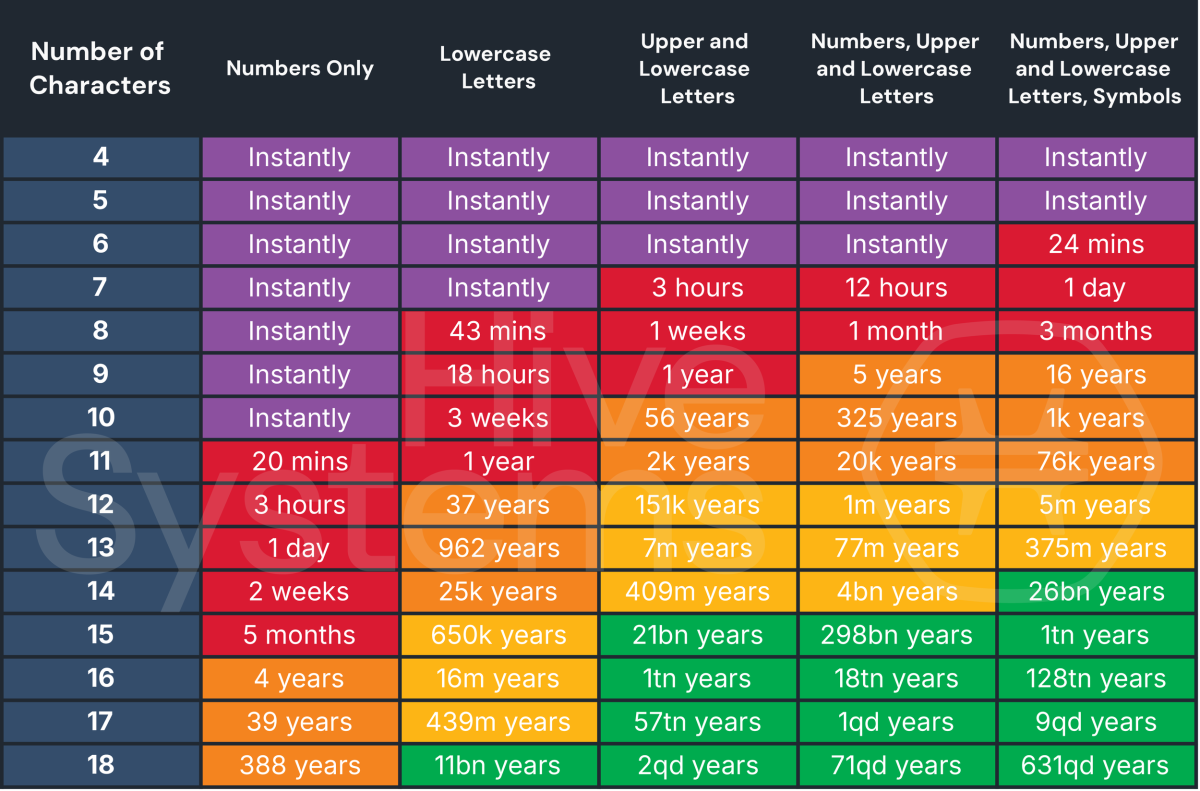
And if you’re looking at the table showing the work of 12x RTX 5090s, thinking, “Okay, who would ever wait years to crack a password?” In fact, a hacker may not need to wait at all. Hive Systems also ran an analysis of how fast brute-forcing could go if the task were given to AI.
(It’s not good.)
When you put enterprise-grade hardware on the job, the graphics cards that trained ChatGPT-3 could guess an 8-character password made of lowercase letters in an hour. The hardware that trained ChatGPT-4? 43 minutes. And the hardware that runs ChatGPT? 30 minutes.
As for a more complex 8-character password—one that has numbers, upper- and lowercase letters, and special characters—an AI tool like ChatGPT could guess it in just 2 months. If that’s all that stands between a determined hacker and a crypto wallet, well.
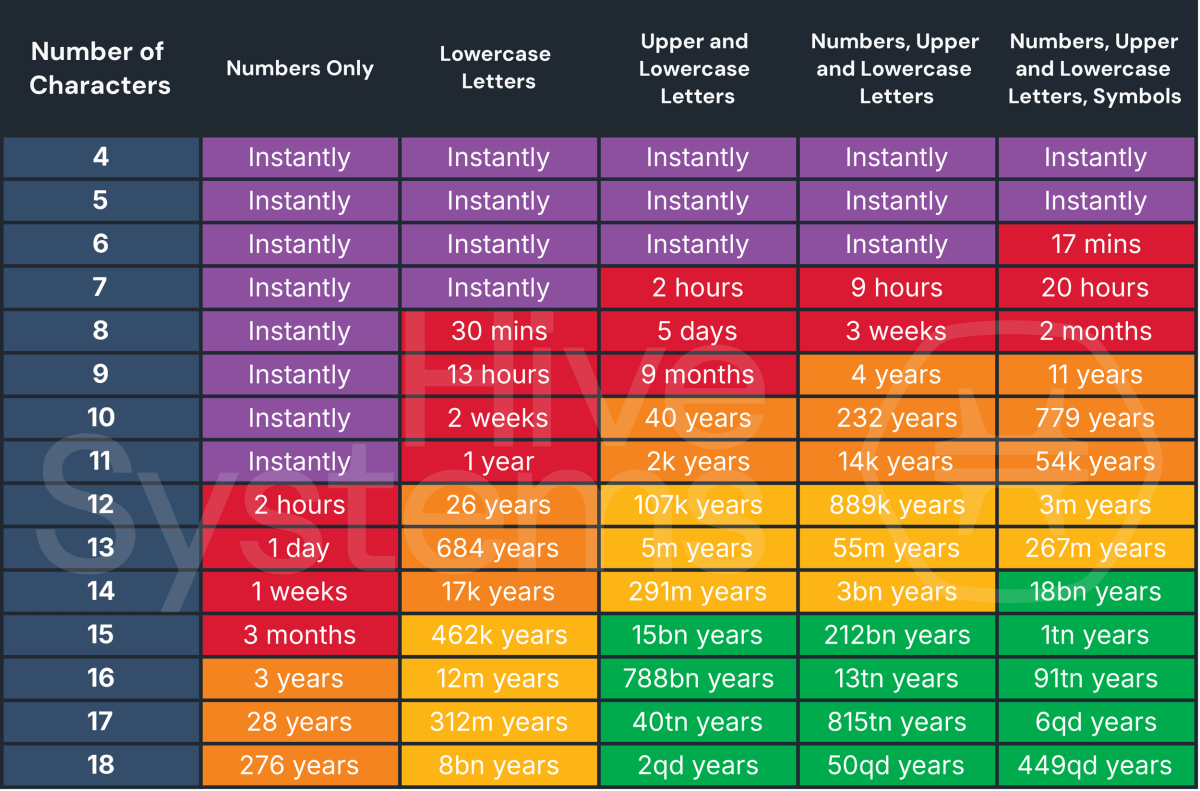
Speaking of which, Hive Systems thought of the same thing. If a home-brew hacker turned a squadron of 5090s on password data from the 2022 LastPass breach, here’s what the collateral damage could look like:
In this slideshow, the first image shows an estimate of what happens when you put the hardware behind ChatGPT-3 to work cracking passwords. The second shows the estimate for ChatGPT-4’s hardware, and the final image shows the likely result of putting the hardware running ChatGPT on the task.
Why so quick? At the time of the breach, LastPass hadn’t run passwords through as many rounds of hashing (iterations), which strengthens the encryption of the password. The default for some older accounts was still just 5,000 iterations—far below the hundreds of thousands recommended at the time. In other words, less work for powerful hardware.
The good news
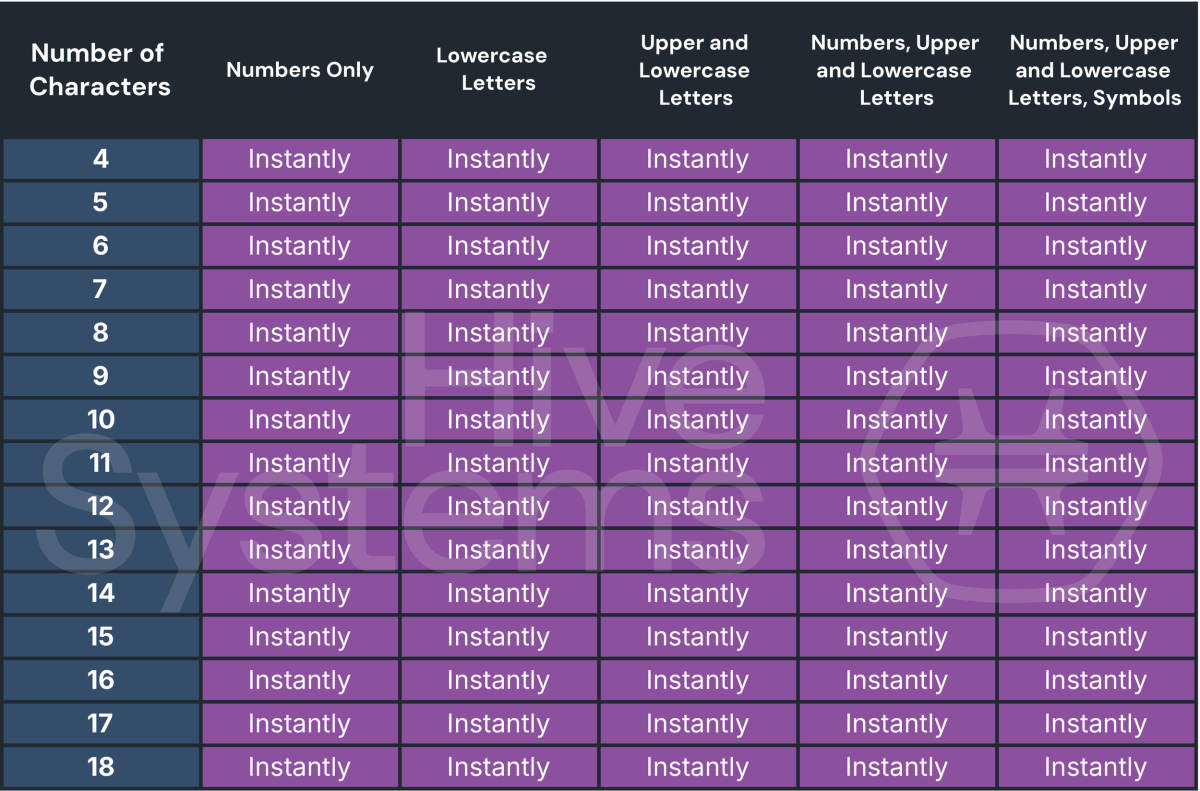
Reading the charts can be scary if you’re an 8-character password kind of person—but comforting if you lean on longer, more complex passwords. At the moment, anyone rocking a 16-character password with numbers, upper- and lowercase letters, and special characters is not only sitting safe from a small collection of 5090s but also ChatGPT.
As compute power continues to rise (and the prospect of quantum computing draws closer), these guidelines will change. You can get ahead of some of it by choosing longer, more complex random passwords now—let a password manager handle the hard work of both generating and remembering them. You can use software that stores the data locally on a device if you’re not comfortable storing the data in the cloud.
OUr Favorite Password Manager
Also enable two-factor authentication on all accounts that allow it. If your password ever falls to cracking software, it’s a second line of defense against unauthorized access. A method like a hardware key (e.g., Yubikey) is the strongest form because it’s phishing resistant. But you’re still better off using an app that generates one-time passwords (OTP) than nothing.
Your best bet? Switching to passkeys as your primary way of logging into your accounts. They can’t be brute-forced as passwords are, and they’re also phishing-resistant—a double win. The only real hazard with passkeys is losing the device you’ve stored them on (e.g., your phone).
But with so many easy ways to store passkeys, it’s simple to create multiple backup ones. And if nothing else, you can leave a super long, complex, and random password + 2FA active on an account, then store that info in a password manager and 2FA app that you fully control. Afterward, just leave them be unless you need emergency access to your accounts.
Jelentkezéshez jelentkezzen be
EGYÉB POSTS Ebben a csoportban

The Windows 11 Start menu is a functional menu, but not much more. Do

Many Windows users rely on CCleaner to tidy up their systems and remo

The last few months of PC news has been dominated by one thing: US pr

Crime does pay. It’s the motivator behind ransomware and extortion sc


If you’re a keen-eyed reader, you may recently have spotted the Copil

Every so often, I end up with a new gadget, accessory, or tool that’s