Following the huge wave of ransomware last year, there’s now increasing reports of completely new tricks used by hackers and cybercriminals to gain access to computer systems, devices, and networks.
Many of these tricks exploit existing vulnerabilities in applications and operating systems, but these perpetrators are also developing completely new approaches that combine technical procedures with social engineering to achieve their goals.
To recap if you’re unaware: social engineering is when a malicious person exploits you through helpfulness, trust, fear, or respect in an attempt to manipulate you into doing something.
Further reading: Key signs of social engineering to look for
Examples of social engineering include: a work email purporting to come from your boss with a payment order for a large sum to a foreign account; a WhatsApp message from someone pretending to be your relative in need of money; or a phishing email that claims to be your bank asking you to click a link with scary consequences if you don’t.
Here are some of the latest scams and techniques used by criminals that you need to know about—and how you can protect yourself.
1. The zero font trick
It’s possible to set the font size of email text to zero using HTML code. In this way, the text is present but not visible to the eye.
A few years ago, criminals used this trick to insert invisible text into messages in order to fool the spam and virus detection mechanisms of email providers and mail programs.
They used this technique to insert harmless words and phrases into the email body to make the message appear safe, thus outwitting the email providers’ malware filters.
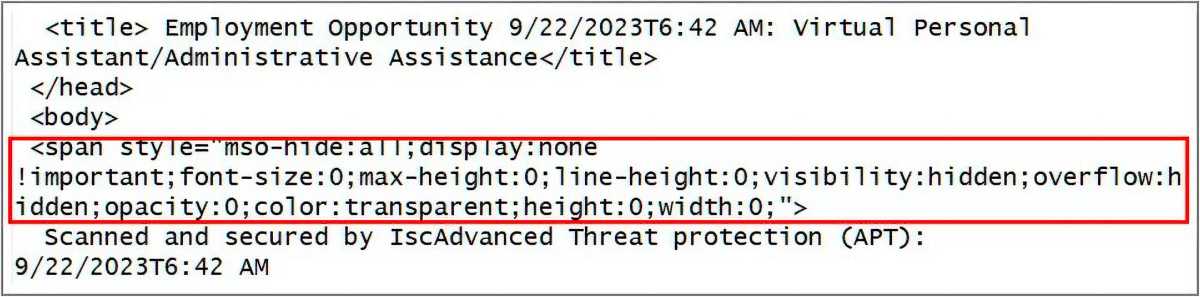
For emails in HTML format, it’s possible to set the font size to zero. The corresponding attribute is “font-size:0”.
For emails in HTML format, it’s possible to set the font size to zero. The corresponding attribute is “font-size:0”.
IDG
For emails in HTML format, it’s possible to set the font size to zero. The corresponding attribute is “font-size:0”.
IDG
<div class="scrim" style="background-color: #fff" aria-hidden="true"></div>
</div></figure><p class="imageCredit">IDG</p></div>Last autumn, security researcher Jan Kopriva became aware of a new version of the zero font trick. Hackers used it to attack Microsoft Outlook users, exploiting a feature of the program’s email display.
The issue is that Outlook happens to display zero font text in its list view, but not in the email preview. The malicious senders therefore placed the zero-point text in the message: “Isc Advanced Threat protection: This message has been scanned for threats.”
“Isc” stands for the Internet Storm Center, an organization of the SANS Institute that monitors malicious activity on the internet. The reference to the alleged malware scan made the email seem trustworthy to recipients, so they were more inclined to open it and trust what it says.
However, the message actually contained a link to a fake website that requested the visitor’s access data:
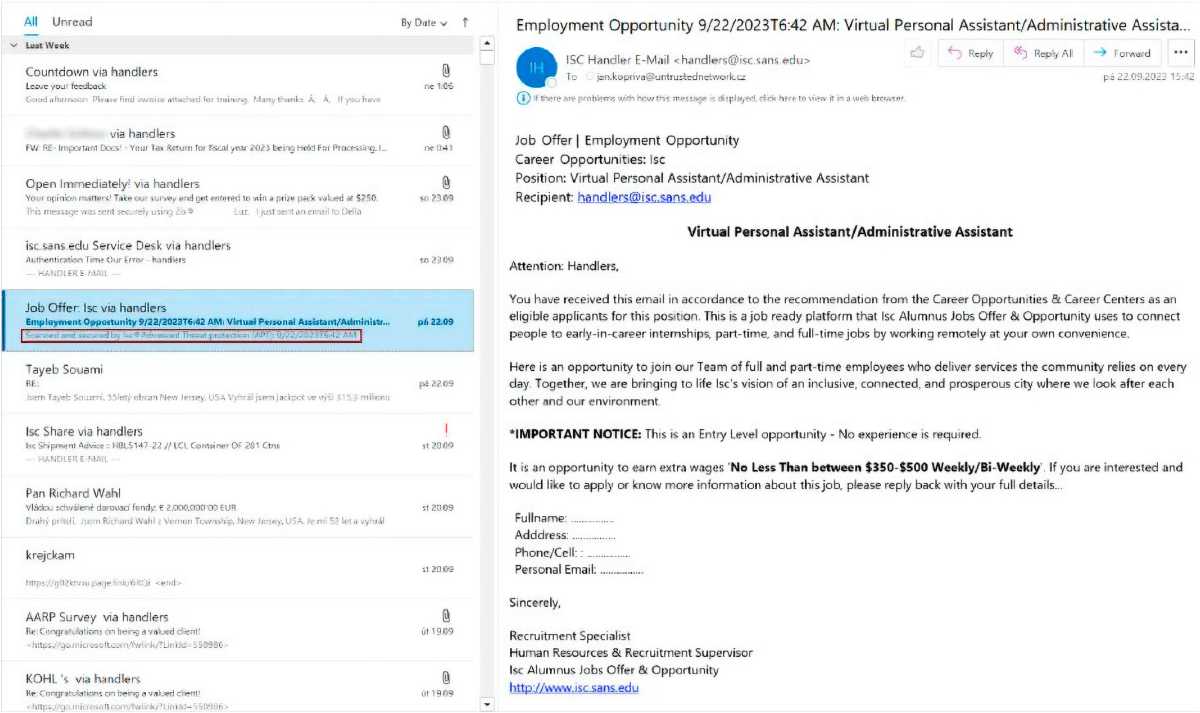
Outlook displays zero font text in the list view. The email has supposedly already been scanned for malware threats and is harmless. It therefore appears trustworthy to the recipient.
Outlook displays zero font text in the list view. The email has supposedly already been scanned for malware threats and is harmless. It therefore appears trustworthy to the recipient.
IDG
<div class="lightbox-image-container foundry-lightbox"><div class="extendedBlock-wrapper block-coreImage undefined"><figure class="wp-block-image size-large enlarged-image"><img decoding="async" data-wp-bind--src="selectors.core.image.enlargedImgSrc" data-wp-style--object-fit="selectors.core.image.lightboxObjectFit" src="" alt="In der Listenansicht zeigt Outlook Zero-Font-Text an. Angeblich wurde die Mail bereits auf Malware-Bedrohungen gescannt und ist unbedenklich. Für den Empfänger wirkt sie daher vertrauenswürdig." class="wp-image-2347784" width="1200" height="714" loading="lazy" /><figcaption class="wp-element-caption"><p>Outlook displays zero font text in the list view. The email has supposedly already been scanned for malware threats and is harmless. It therefore appears trustworthy to the recipient.</p> </figcaption></figure><p class="imageCredit">IDG</p></div> </div></figure><p class="imageCredit">IDG</p></div>How to protect yourself:
- Learn how to spot scam emails and messages.
- Even with emails that claim to be from reputable senders, remember that they could be fake.
- Hover over every link to confirm the destination address before clicking—and even then, don’t click unless absolutely necessary. It’s better to navigate to the site manually if you can.
- If you have any doubts that an email actually came from a particular sender, give them a quick call to confirm.
2. Vulnerabilities in 2FA/MFA
Two-factor authentication (2FA) or multi-factor authentication (MFA) protects users against attacks on their login credentials. With 2FA enabled, it’s much harder to hack an account.
So, hackers are increasingly trying to access the cookie files that are created during the login process that certify correct authentication.
With these session cookies, it’s possible for a user to log in just once and continue accessing various services. As soon as the user logs out, the session cookie is deactivated.
Further reading: How to use 2FA the right way
Various malware programs are now exploiting a vulnerability in the Google login process to reactivate expired session cookies. In this way, they can freely access all Google services belonging to a user.
This works even if they’ve changed their password in the meantime. However, this requires the malware to have access to the user’s computer.
How to protect yourself:
- Understand how malware infections happen. Don’t open attachments in suspicious emails. Don’t click on links in emails. Don’t download apps from illegal or suspicious sites.
- Shut down your computer when you don’t need it.
- Apply security patches for Windows and other programs immediately and always keep your software up to date.
3. Deepfakes from your boss
Traditionally, the boss scam is where your “boss” instructs you to transfer a large sum of money to an unusual account, but the “boss” is actually a hacker who’s sending your fraudulent emails or texts.
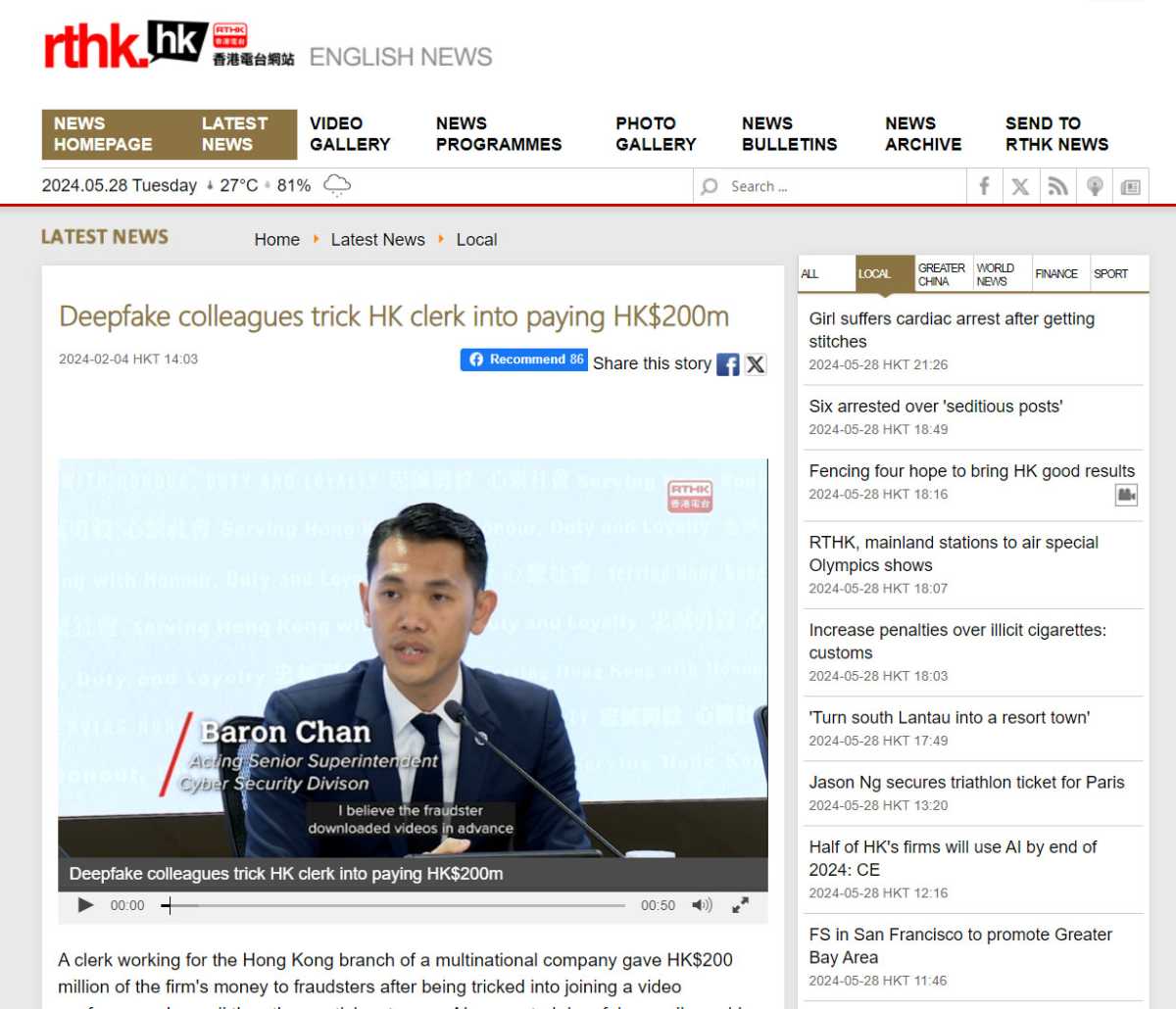
A new variant has now come to light in Hong Kong, where hackers invited their victim to a video conference by email. However, no real people were waiting for him there—only deepfakes of colleagues from his company. (A deepfake is an AI-generated impersonation of a real person.)
These deepfakes instructed the victim to carry out 15 transfers totaling 200 million Hong Kong dollars. (About $26 million USD.) The victim only realized that he had been scammed when he later spoke to his boss.
Autentifică-te pentru a adăuga comentarii
Alte posturi din acest grup

Interest in Sonos’s smallest portable speaker is heating up—literally

Free alternatives may exist for Microsoft Office components, but some

E-commerce giant Amazon is now expanding its automotive business to i


As expected, by 2028 your PC will be internally passing a terabyte’s

Want ad-free streaming without paying through the nose for Netflix or

Microsoft is reportedly testing a new feature in the taskbar called “
